Recently I encountered a scenario where the client had a requirement to connect to AWS public services via direct connect.
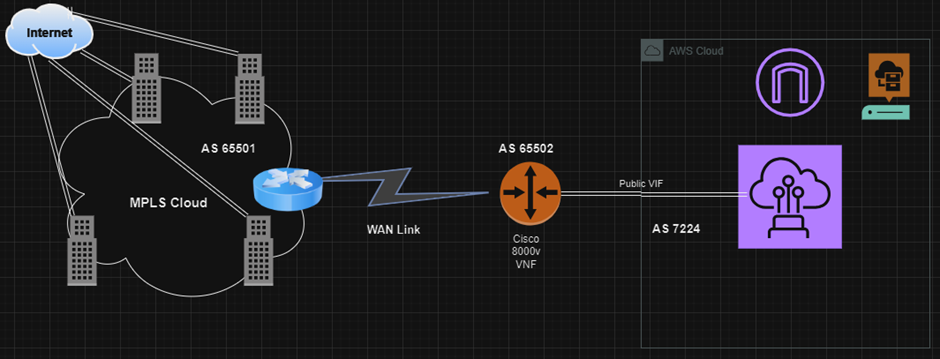
The requirement was to have multiple sites on MPLS that connect to a Global WAN provider platform via a Cisco 8KV VNF router. The service provider connects to AWS for direct connect. All the sites should break out to the internet locally but for the AWS public services need to route via MPLS and AWS connect.
To achieve this a public VIF needs to be created on AWS to access the services. The routes from all the office sites via MPLS will be learned on the C8KV router over BGP that will hide NAT’ed behind a Public IP provided by the ISP. Also, an additional /30 public IP subnet needs to be assigned for the BGP between C8KV and Public VIF.
When working with AWS public VIF to establish BGP peer trying and advertise the public IP addresses provided by the ISP, AWS would need a LOA from the provider (an acceptance email) confirming the public IP addresses can be used on the AWS network. This is because AWS would have one of the IP addresses from the /30 assigned to the public VIF for BGP.
AWS advertises all its public subnets over BGP, hence we need to apply the necessary prefixes on the C8KV and permit the routes that host the services we are trying to access.(https://docs.aws.amazon.com/vpc/latest/userguide/aws-ip-ranges.html),
AWS public prefixes must not be advertised beyond the scope of the current direct connect connection as there is a risk of AWS subnets being advertised over the internet from anywhere else that could cause issues. AWS advertises all the subnets with a NO-EXPORT tag to ensure the prefixes are not further redistributed across BGP to different ASNs than what it is peered with.
More details on how to restrict the advertisement of the prefixes with community tags to specific AWS regions is provided in the link below.
AWS does not recommend this but in this scenario, we need to advertise the public prefixes to MPLS for sites to route traffic for the AWS via direct connect instead of local internet breakout.
- Create a community list to match the no-export tag via a permit statement:
ip community-list standard <AWS> permit no-export
- On the route-map attached to BGP peer towards AWS, add to the permit statement the following set command to strip the no-export tag:
route-map AWS permit 5
set comm-list <AWS> delete
This will ensure that the routes installed on C8KV that are without the no-export tag.
Leave a Reply